You're probably familiar with the concept of a Minimum Viable Product (MVP) if you're creating a software product, SaaS platform or IoT device. But did you know there is also something called the Minimum Viable Secure Product (MVSP), which means your product meets the minimum security requirements every product should adhere to? Let's explore MVSP with 4 questions.
What's a MVSP?
MVSP is a security baseline created by industry giants like Google, Okta and Salesforce. It's a minimal list of requirements that every software product should meet and a great resource meant for businesses of any size, not only for large businesses. If your product is being used, then it should honestly meet these requirements.
What's it good for?
First and foremost, meeting these requirements will noticeably increase the security of your product and reduce costly security incidents in the long run. Many recent regulations, such as the GDPR or M-22-18, require a minimum level of security hygiene from certain companies, and chances are high you are among them. In the future this will only become stricter with new regulations being implemented, such as NIS-2.
Secondly, your sales team will have a security checklist they can provide to potential customers. Once you start selling to bigger corporations, proof that you take cybersecurity seriously becomes very important. If you're too small for a security certification, having the MVSP checklist checked off can act as enough proof of your good cybersecurity hygiene to land the contract.
Thirdly, if you're looking for vendors, ask them if they meet the requirements on this list. If they cannot answer that question affirmatively, it might be good to consider other options. The security of your product also depends on the security of the partners you work with.
Is it hard to meet these requirements?
It depends. If you have experience developing secure software, you will probably already meet several if not most of the 25 requirements without knowing you do. Many requirements describe what's considered current best practices. Let's see some examples:
- 1.1 Vulnerability reports:
- Publish the point of contact for security reports on your website.
- Respond to security reports within a reasonable time frame.
- 2.2 HTTPS-only:
- Redirect traffic from HTTP protocol (port 80) to HTTPS (port 443).
- Scan and address issues using freely available modern TLS scanning tools.
- Include the Strict-Transport-Security header on all pages with the includeSubdomains directive
- 3.1 List of data: Maintain a list of sensitive data types that the application is expected to process.
As you can see, these examples are practices you might already be doing if you take security seriously, and if you don't, aren't that hard to implement.
Where do I start?
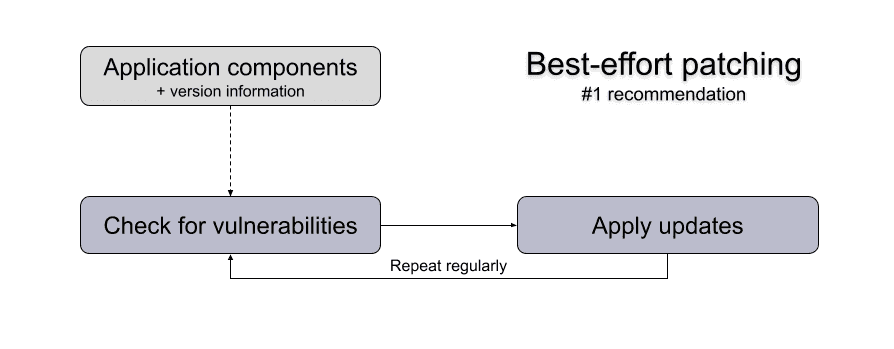
Take a look at the checklist. You'll see that the requirements generally fall in two groups: the ones requiring technical implementation and the ones prescribing a high-level process. It's generally easier to start with the ones requiring technical implementation as developers are able to make quick work of them.
For the processes, some are easy, but others might require more security experience to implement them correctly. If you're unsure, contact a professional to help you implement these processes or take a look at our services or contact us.
Conclusion
MVSP is meant for businesses of all sizes and will help you start implementing cybersecurity best practices. The items on the list are minimal and very relevant. If you're uncertain where and how to improve Application Security, the MVSP checklist is a great place to start!